The tech world in general, and the Internet of Things space in particular, is extremely dynamic. New tools and products are emerging regularly, while IoT systems are becoming increasingly complex. All of this opens up entirely new opportunities for users. However, along with these advancements, security threats are growing as well. Managing and securing complex networks is much more challenging than it used to be some years ago. At the same time, cybercriminal tools are becoming more sophisticated.
That’s why it’s so important to pay serious attention to security in IoT today. How can you protect your devices and sensitive data? That’s exactly what we are going to explore in our article.
IoT security: What is it?
Before we proceed to consider IoT security challenges and solutions, let us provide the most basic definition of this term.
IoT security refers to the strategies, technologies, and best practices used to protect smart devices of different types (from smart thermostats to autonomous vehicles) and the networks that they are connected to.
Unlike traditional computers, many IoT devices have limited processing power and memory. Therefore, it becomes more difficult to implement robust security protocols.
Apart from this, smart devices often operate autonomously and are deployed in remote locations. This complicates software updates and management, which is an additional pitfall for ensuring security in IoT networks.
Importance of IoT security in 2025
The world is moving deeper into the era of hyper-connectivity. Amid this transformation, proper protection of IoT networks from cyberattacks becomes a foundational requirement.
Here are some arguments that clearly demonstrate the significance of securing IoT devices.
- Growing attack geography. Today, billions of IoT devices are functioning all over the globe. Each of them can become a potential entry point for cyberattacks. Many connected devices still have limited security features. This makes them pretty easy targets for hackers. If just a single device is compromised, it can represent a serious threat to an entire network.
- Increasing complexity of threats. Cybercriminals actively use advanced technologies like AI, machine learning, and automation tools to launch large-scale, sophisticated attacks. For example, they can create botnets based on hijacked IoT devices. Such botnets can disrupt services, steal sensitive data, or perform DDoS attacks on entire systems.
- High-stakes industries and highly sensitive data. Businesses increasingly depend on IoT for real-time data and automation. Given this, IoT breaches can have real-world consequences. In such industries as healthcare or transportation, not just data, but also human safety is at risk.
Quick overview of today’s IoT security landscape
Statistics further underscore the growing need for IoT security solutions. More than half of all IoT devices currently in use contain critical vulnerabilities that can be exploited by hackers. On average, businesses face costs of $330,000 per IoT-related incident. These losses include not only immediate damages but also long-term consequences such as reputational harm and regulatory fines. Спросить ChatGPT
Recent analyses indicate a notable increase in device vulnerabilities across IoT, IIoT, and IoMT sectors. For instance, Forescout's 2025 report highlights a 33% rise in average device risk scores compared to the previous year. According to the research, such countries as Spain, China, and the UK experience the highest risks in terms of IoT vulnerabilities.
The global IoT security market hit the mark of $24.2 billion in 2024. Now, it is projected to grow to $56.2 billion by 2029, reflecting a CAGR of 18.4% over the forecast period.
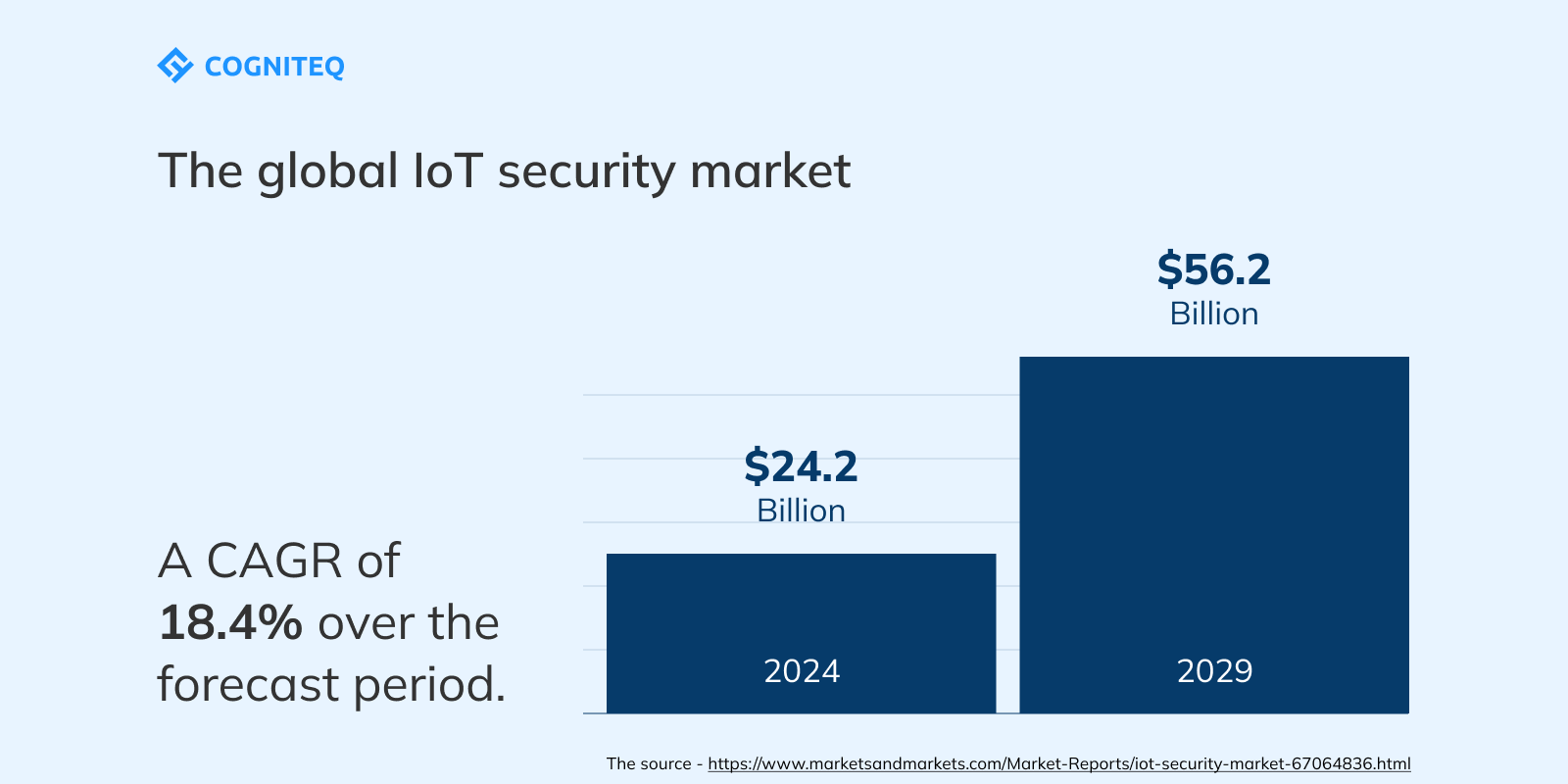
Today, there are such strong market drivers as new IoT security regulations and an increasing number of IoT device incidents. Nevertheless, there are also factors that slow down market development. For example, limited awareness of IoT security problems and low budgets of small and medium businesses, especially in developing countries, are among them.
The most common IoT security risks
If you are thinking about how to secure IoT devices, first of all, you should understand the potential issues that you may face.

Weak passwords
Not all users clearly understand what strong passwords really mean. Quite often, they choose very simple combinations of repetitive numbers for their passwords. Moreover, a lot of IoT devices still ship with default passwords, and some users just leave them as it is. However, this makes them susceptible to unauthorized access. Attackers can easily exploit these credentials to gain control over devices.
Unencrypted data transmission
Many IoT devices transmit data without proper encryption. This makes sensitive information an easy prey for cybercriminals. A lack of secure communication channels can lead to data breaches and unauthorized data manipulation.
Insecure APIs
APIs in IoT devices can be poorly secured, providing attackers with pathways to infiltrate systems. Weak authentication and authorization mechanisms in APIs can lead to unauthorized data access.
Lack of firmware updates
Devices often operate with outdated firmware. Due to this, attackers can exploit existing flaws, compromising device integrity and network security.
Shadow IoT
Unauthorized or unmanaged IoT devices, known as Shadow IoT, pose significant risks because they often operate outside the control of IT departments. These devices can introduce vulnerabilities and serve as entry points for cyberattacks.
Lack of standardized security protocols
The IoT ecosystem is very fragmented today. Many manufacturers use their proprietary protocols and systems. This inconsistency leads to gaps in interoperability and makes it difficult to implement uniform security policies across networks.
Cloning and spoofing of devices
Attackers can create counterfeit versions of legitimate IoT devices or spoof device identities. By doing this, they can gain unauthorized access to data or entire networks. This can lead to data leaks or system manipulation.
Physical tampering
Many IoT devices are deployed in public or remote locations. Therefore, they are vulnerable to physical tampering. This can result in data theft, firmware replacement, or device hijacking.
Security in IoT: Best practices
At Cogniteq, we work with different technologies, and IoT is one of the fields where we have the strongest expertise. Over the years of working in this field, we’ve managed to find a highly efficient approach to securing IoT networks. These security principles will help you reduce IoT security risks at your organization.
- Cooperate with experts. Security is a very important aspect. That’s why you need to make sure that specialists who are responsible for it have relevant knowledge and expertise. If you are going to work with external partners, you need to find a team that specializes in IoT security services.
- Educate users and staff. If you want to make sure that your devices and systems stay secure, you should make user and staff training on IoT an integral part of your security efforts. You should increase security awareness and promote the culture of accountability.
- Bear in mind that security is always evolving. For having a well-protected system, it’s not enough just to buy high-quality devices and power them with secure software. Threats and malicious actors are constantly adapting. They develop new tactics to exploit vulnerabilities and disrupt systems. You should understand that no system is ever completely immune. It is required to stay proactive and continuously monitor the security of your devices and systems.
- Choose trusted vendors. When you are considering various off-the-shelf devices for your systems, always prioritize those manufacturers that offer regular updates, public security documentation, and long-term support. Verify whether the devices under consideration are compliant with recognized standards like NIST or the Cyber Trust Mark.
- Always change default credentials. We recommend you immediately update default usernames and passwords on all IoT devices. It is essential to introduce strong, unique passwords and enable multi-factor authentication (MFA) where available.
How to secure IoT devices: Practical recommendations
Want to protect your connected devices from cyber threats and ensure the integrity of your systems? The following practical tips will help you address modern IoT security challenges.
Regularly update your firmware and software
After activating and connecting your smart devices, you need to check for and install updates from the manufacturer. You can also enable automatic updates to ensure timely patches for known vulnerabilities.
Segment your IoT network
It is recommended not to connect your IoT devices to the same network that your critical systems or personal computers are connected to.
Disable features that are not used
You should turn off those services that are not actively in use, like remote access or Bluetooth. Thanks to this, you can reduce the number of potential entry points for cybercriminals.
Always encrypt data in transit
It is vital to ensure that your devices support and use encryption protocols like TLS or SSL for communication.
Continuously monitor device activity
We recommend you use tools that will be able to detect any suspicious activities on the network. Today, there are powerful ML solutions that can timely identify and notify about any signs that indicate potential cyberattacks.
Use secure APIs
If your devices interact with any APIs, use proper authentication for them. Apart from that, API traffic monitoring for abuse or anomalies is a must.
Control physical access
Install devices in secure locations to reduce the risk of tampering.
What you should know about IoT security solutions?
To protect your connected devices, you can implement IoT security solutions.
These are tools, technologies, and practices designed to protect IoT networks and smart devices from cyber threats.
Key features often include strong authentication protocols, data encryption, secure boot processes, automated software updates, network segmentation, continuous monitoring, and runtime protection. All of them work together to enhance overall IoT security.
Planning to launch your own IoT solution?
Our professional team of developers will help you build and implement security tools of any complexity based on your specific business needs.
Perks of using IoT security tools
Still unsure about whether to turn to professional IoT security services and implement relevant tools to protect your systems? We have prepared some arguments to prove their value.
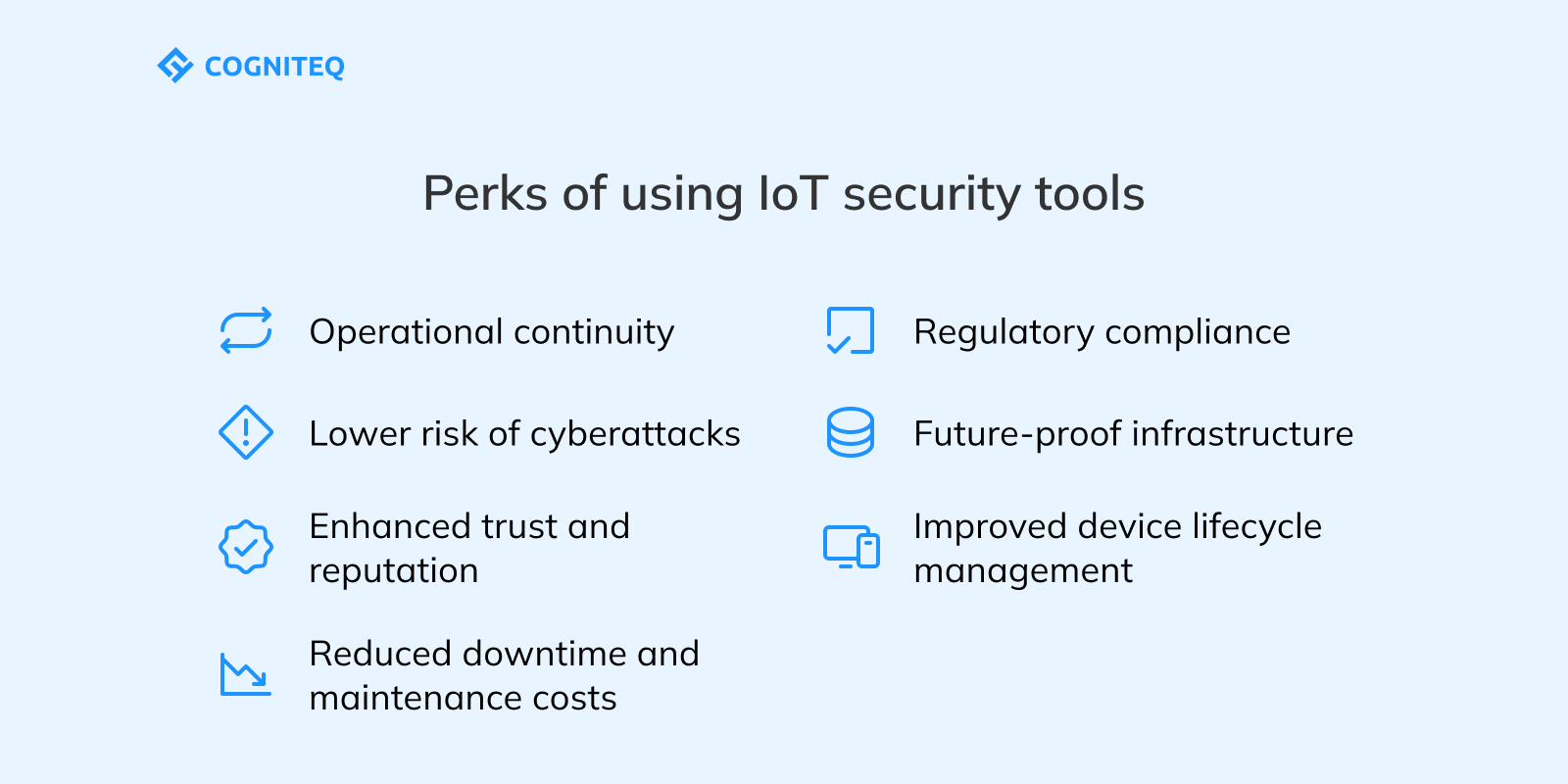
- Lower risk of cyberattacks. Security solutions help find and block threats of different types, including malware, ransomware, or unauthorized access to sensitive systems. The main benefit here is that such issues can be identified before they cause real damage.
- Regulatory compliance. Many industries require strict adherence to data protection laws like GDPR or HIPAA. Security tools can help organizations stay compliant and avoid serious expenses caused by fines or legal consequences.
- Operational continuity. Thanks to the timely prevention of device outages and service interruptions caused by security breaches, organizations can leverage uninterrupted business operations.
- Enhanced trust and reputation. Customers and partners are more likely to trust organizations that demonstrate a strong commitment to data security.
- Improved device lifecycle management. In addition to risk detection functionality, IoT security solutions often include tools for monitoring, updating, and decommissioning devices safely. All this minimizes risks from outdated or forgotten equipment.
- Future-proof infrastructure. Many security platforms can adapt to evolving standards and threats over time. This allows systems to remain secure even when new IoT attack methods emerge.
- Reduced downtime and maintenance costs. It may seem that the introduction of security tools just adds extra costs. In reality, such solutions can help you save money. They are designed to prevent breaches and misconfigurations. As a result, with them, you can avoid costly outages, emergency fixes, and unexpected maintenance.
Final word
The IoT space continues to expand and transform industries worldwide. With billions of interconnected devices handling everything from personal data to critical infrastructure, the need for proper IoT security has never been higher. The evolving threat landscape demands comprehensive security strategies.
If you have an IoT network, one of the first things that you should do to protect it is to understand the existing risks and find out how you can address them. By implementing best practices and introducing advanced security solutions, you can build a resilient system.
With hands-on experience in building secure IoT ecosystems, our team knows how to protect your connected devices, networks, and data from evolving cyber threats.
It doesn’t matter whether you are launching a new IoT product or looking to enhance the security of an existing system, we can provide our professional assistance at every stage. Contact us to learn more about our services and expertise.
FAQ
What are the biggest IoT security concerns in 2025?
Today, the most serious IoT security concerns include unauthorized access due to weak authentication protocols and insecure data transmission. Device fragmentation is another challenge, as inconsistent security measures create extra vulnerabilities. Moreover, the increasing use of AI in attacks enables more sophisticated exploitation of IoT systems.
What are the best practices for small businesses to protect IoT devices?
It is worth starting with introducing strong passwords, firewalls, and regular software updates for all IoT devices. The use of device-specific authentication, data encryption, and disabling unused features can also greatly reduce vulnerabilities. Moreover, to minimize the risk of breaches, it would be helpful to set up a segmented network for IoT devices and train staff on basic cybersecurity practices.
What industries face the highest risks from IoT security threats?
Sectors like healthcare, critical infrastructure, and manufacturing that rely on connected devices for real-time operations are the most vulnerable to security risks. These industries often work with sensitive data, which makes their systems look appealing to cybercriminals. Inadequate device security may further increase their vulnerability to breaches.
What role does AI play in enhancing IoT security?
With its capability to detect unusual patterns and anomalies in real time, AI greatly strengthens IoT security. AI-powered tools are used to identify potential threats before they cause harm. It enables predictive threat analysis and automated responses. This approach reduces the time required to contain cyberattacks.
What new IoT security regulations have come into force in 2025?
In 2025, significant IoT security regulations have been enacted globally. For example, the newly introduced US Cyber Trust Mark helps consumers easily identify IoT devices that meet specific cybersecurity standards. Meanwhile, according to the European Union's Cyber Resilience Act (CRA), all IoT devices that are available in the market must satisfy the cybersecurity requirements.























































