
Honeywell
Web app for data collection terminals
Honeywell, USA.

Request
Result
Technologies
- AngularJS
- .NET
- TypeScript
- ASP.NET
- C#
- Karma
- MS SQL
- Jasmine
- EF Core
Result
Results
-
Functionality delivered
The team successfully implemented all required features, including a stable backend and a fully functional admin panel. The interface ensures smooth system operation and meets all technical requirements.
-
Ongoing partnership
The application’s UI is intuitive, user-friendly, and easy to navigate. The client expressed full satisfaction with the project’s implementation, and our collaboration continues actively.
Challenge
Solution
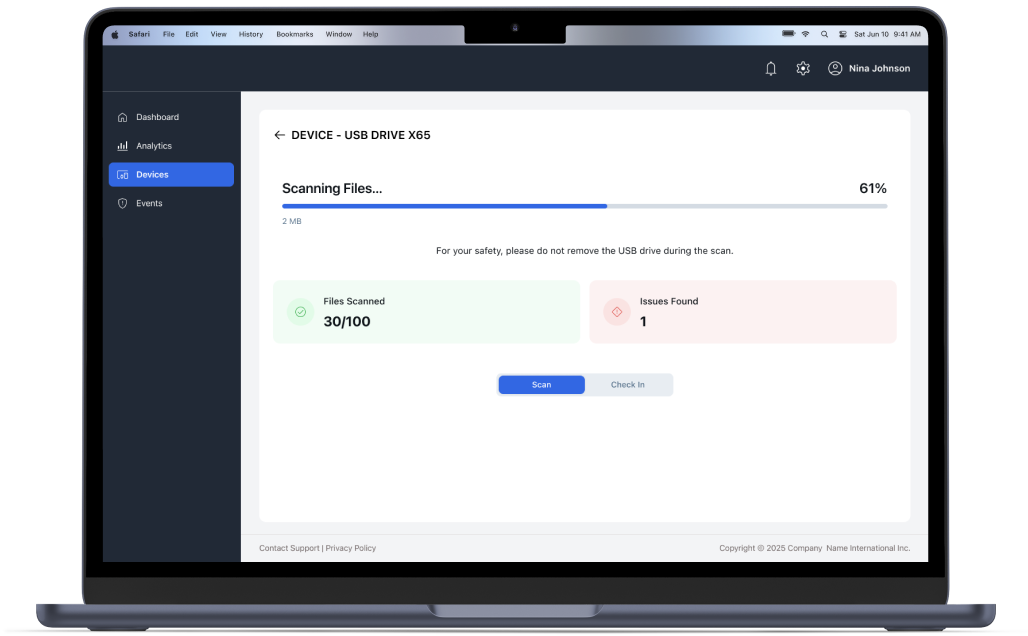
Our team implemented the entire solution from scratch, covering both the frontend and backend parts of the web application (UI + API for the Events solution). The result is a secure, efficient, and scalable platform that allows users from different organizations to track statistics and export data from various terminals.
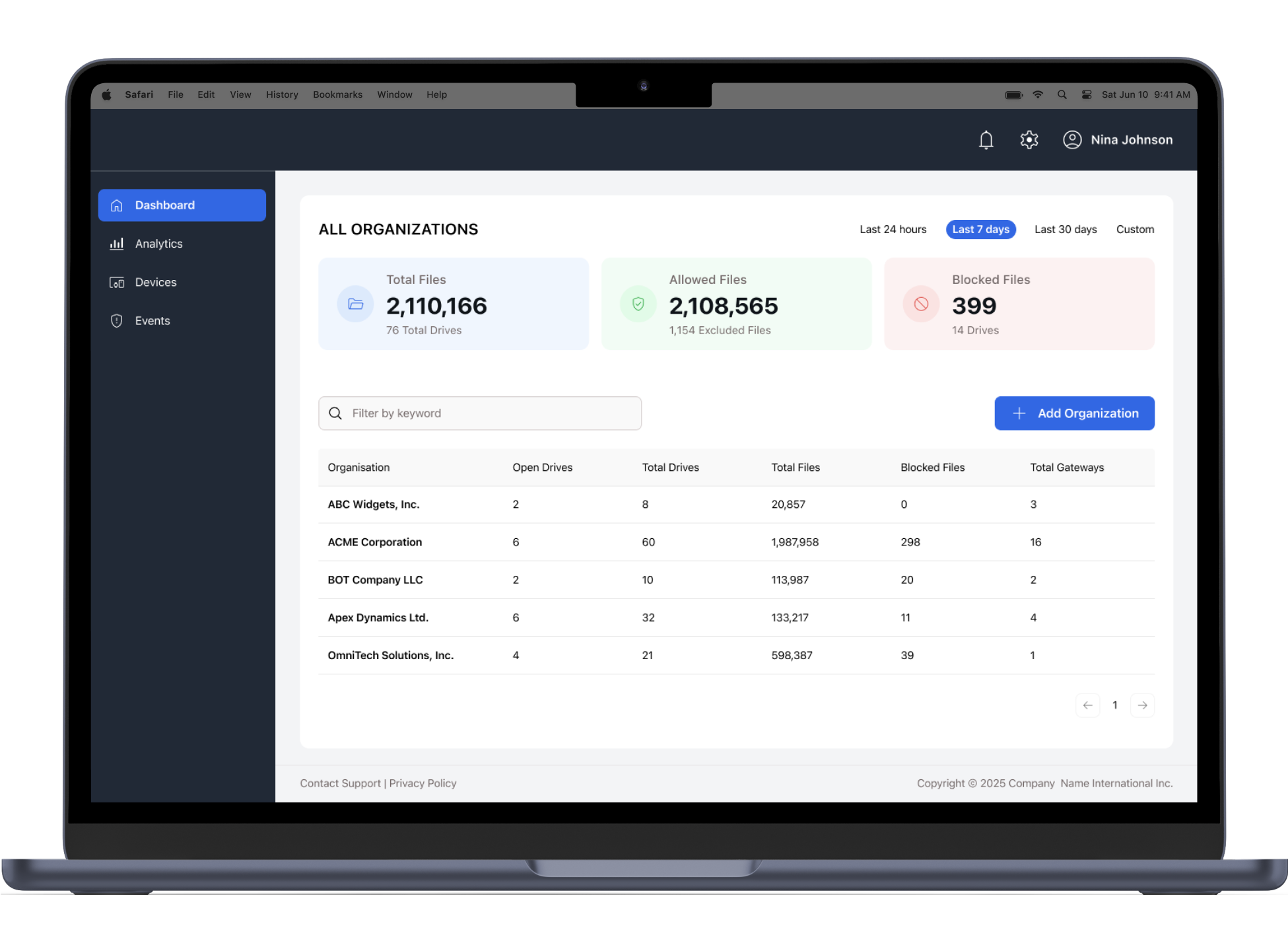
The web application analyzes information stored in the database and displays calculated statistics to the user. It provides a centralized system for monitoring USB activity, managing incidents, and responding to potential security threats. The platform is designed with flexibility and security in mind, making it suitable for enterprises of any size.
Events API
A dedicated API supports the creation and management of Events related to detected threats, providing independent control over incident handling.
Report exporting
Users can generate and export detailed reports on terminal activity and detected threats for further analysis or recordkeeping.
Statistical data classification
The system classifies and presents data by categories such as organization, open drives, total drives, total files, blocked files, and total gateways (terminals).
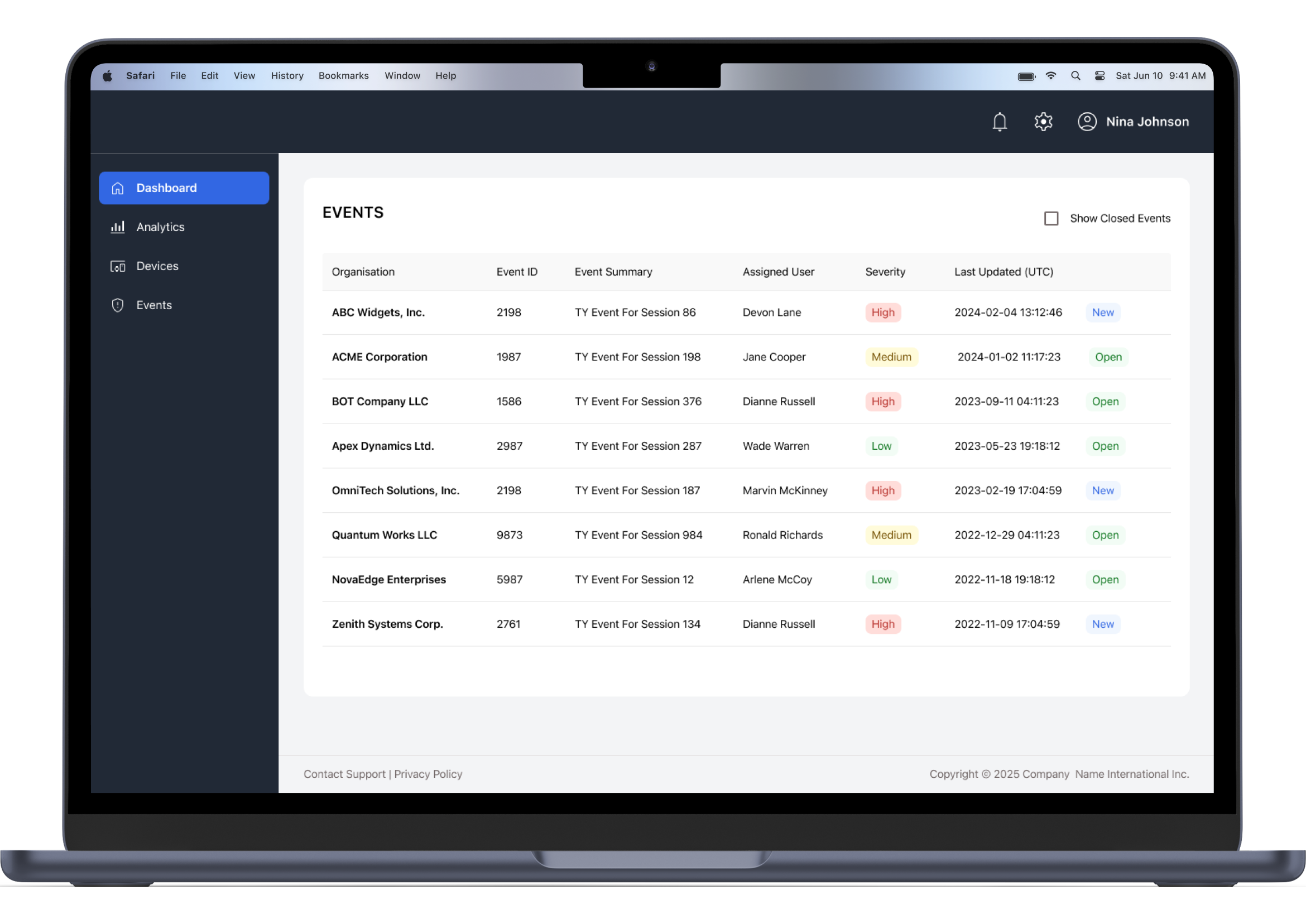
Event management features
Administrators and managers can create Events with defined severity, assign users, and track status updates. Each Event includes the organization name, Event ID, summary (with session number), assigned user, severity level, last update timestamp, and current status (New, Open, Closed). Closed Events are hidden by default, and all open Events related to the organizations the user belongs to are displayed automatically.
Two-factor authentication
Access to the web application is protected by two-factor authentication, requiring users to verify their identity via email.
Role-based access control
Users are assigned roles—admin, manager, or user—ensuring appropriate access levels and responsibilities within the system.
Drop us a line!
Do you have a product idea you wish to bring to life?